Introducing SEToolkit
The Social-Engineer Toolkit is an open-source penetration testing framework designed for Social-Engineering. SET has a number of custom attack vectors that allow you to make a believable attack quickly. It is an open-source Python-driven tool aimed at penetration testing around Social-Engineering.
The attacks built into the toolkit are designed to be targeted attacks against a person or organization used during a penetration test.
Installation
For Kali Linux and Parrot OS, SET comes in-built
For Ubuntu and Debian system
git clone https://github.com/trustedsec/social-engineer-toolkit/ setoolkit/
cd setoolkit
pip3 install -r requirements.txt
python setup.pyUsage
sudo setoolkitNow let us see how to get user credentials using SET
1. Open a terminal and run the following command
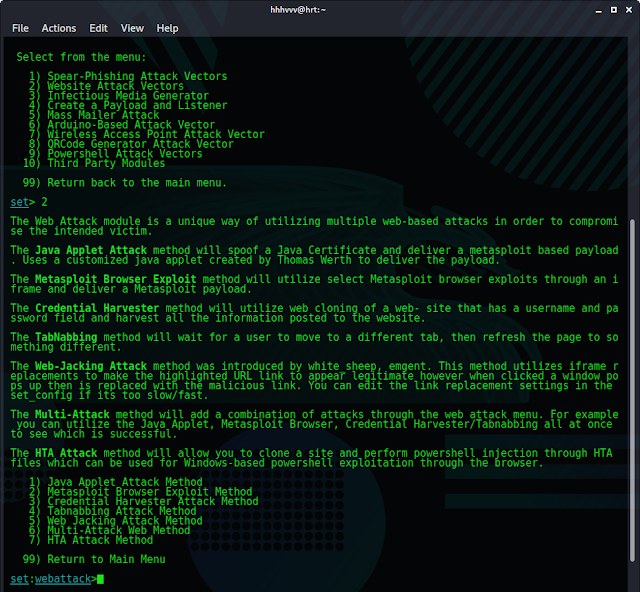
sudo setoolkit2. Now, choose Social-Engineering Attacks from the menu
3. From the new menu, choose Website Attack Vectors
4. To get the credentials of a user, use the option Credential Harvester Attack Method
5. Here we will use Web Templates
6. Now enter your IP address to receive the user credentials. Leave it blank for default address.
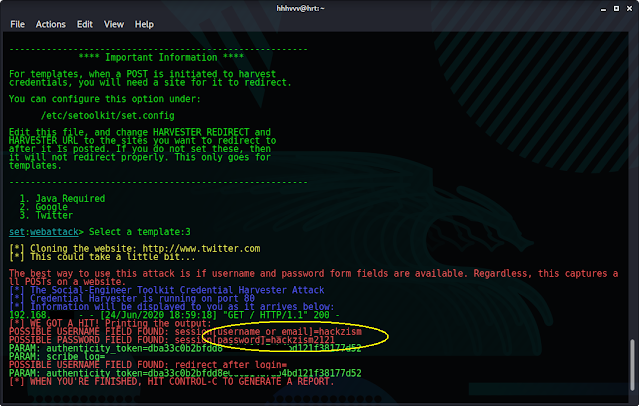
7. Choose a web template. Here, we will use Twitter.
8. Then, open your browser and visit the IP address. You will see the twitter login page and will be asked to enter logon credentials.
When the user enters his credentials, SET will display the username and password.
This information is only for educational purpose and we are not responsible for any kind of illegal activity done by this tool.
Check out similar information gathering tools HERE.
Leave a comment below






Comments
Post a Comment